Infrastructure as code (IaC) is the practice of managing and provisioning infrastructure resources programmatically, using configuration files, scripts, and other software tools. IaC enables software development teams to standardize and automate their infrastructure deployment process
Discover the top 9 best Infrastructure as Code (IaC) Security Tools
PINGSAFE
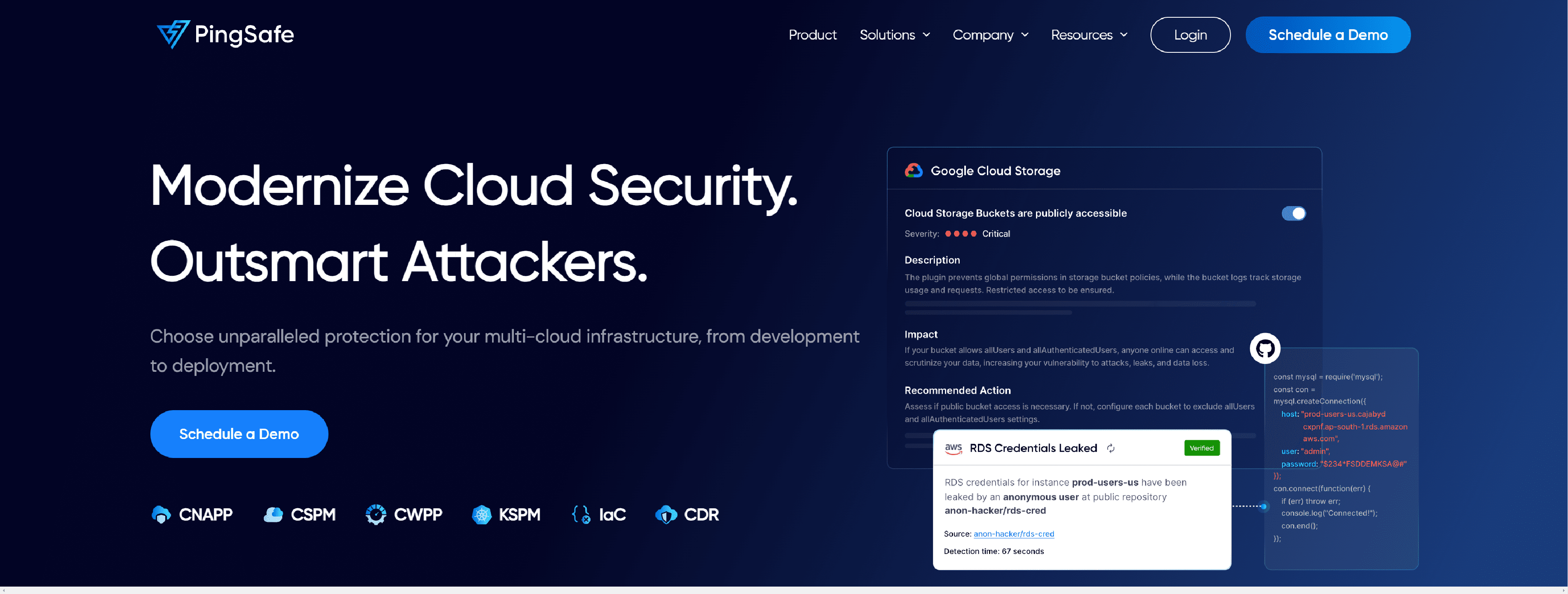
PingSafe – unified cloud security platform with CNAPP, CSMP, CWPP, CDR & CIEM solutions to secure your multi-cloud infrastructure.
- Comprehensive visibility equals better compliance
- Proof of Exploitability with PingSafe
- Eliminate the menace of Secret Leakage
- Shift Left & do right
SNYK
Snyk helps software-driven businesses develop fast and stay secure. Continuously find and fix vulnerabilities for npm, Maven, NuGet, RubyGems, PyPI and more.
- IDE plugins improve developer productivity
- Unified policy engine ensures secure and compliant IaC
- Efficiency from one platform
- IaC security from tools you use
PALOALTONETWORKS

Prisma Cloud scans IaC templates for misconfigurations and exposed secrets across the development lifecycle, embedding security in integrated development environments, continuous integration tools, repositories and runtime environments.
- Continuous governance to enforce policies in code
- Embedded in DevOps workflows and tooling
- Automated misconfiguration fixes via pull requests
BRIDGECREW
Bridgecrew streamlines infrastructure as code security scanning to automatically find and fix misconfigurations in Terraform, CloudFormation, and more.
- Thousands of IaC policies and built-in fixes
- Graph-based and contextual security feedback
- Integrated into developer tools and workflows
FUGUE

Automate cloud security and compliance from infrastructure as code through run-time to go faster in AWS, Azure and Google Cloud environments.
- IaC Security Powered by Open Policy Agent
- Developer Friendly Tools and Integrations
- Centralized IaC Security
- Security for Cloud, Containers, and Kubernetes
- Comprehensive Compliance Coverage
- Visualize Your IaC and Security
ZSCALER

Zscaler, creator of the Zero Trust Exchange platform, helps you reduce business risk while enabling you to realize the promise of digital transformation.
- Prevent IaC misconfigurations
- Integrate scanning in developer workflows
- Get rapid, guided remediation
- Stop configuration drift
- Enforce guardrails
- Generate alerts in near-real-time
ERMETIC

Ermetic delivers Infrastructure as a Code (IaC) scanning as part of a comprehensive and integrated Cloud Native Application Protection Platform (CNAPP).
- IaC Flaws = Increased Attack Surface
- Identify Misconfigurations & Compliance Violations in Code
- Integrate Security into the Development Pipeline
- Built-In Remediation
- Compliance Benchmarks
- Cloud-Native Security across the Full Lifecycle
SONARSOURCE
Sonar employs dozens of IaC specific rules to capture code quality issues in your projects including CloudFormation, Terraform, serverless, lambda, Docker, Kubernetes and more.
- Clean as You Code Methodology
- Sonar Quality Gate Pass/Fail
- Actionable, Highly-precise Analysis Results
- Clear Remediation Guidance
CYRAL
Cyral’s data security governance platform easily authenticates, authorizes, and audits access to your databases in any cloud.
- Centralized and automated provisioning
- Unique credentials and password rotation
- Complete visibility and simple compliance controls
SYNOPSYS
![]()
Synopsys is an IDE-based application security solution that helps you find and fix security issues as you code, without switching tools or interrupting your workflow.
- Code more securely without changing your workflow
- Identify vulnerable open source dependencies
- Fix issues faster with automated remediation
- Write better code and avoid security issues