Zero Trust security is an approach to cybersecurity that challenges the traditional perimeter security model. Rather than assuming that everything inside an organization’s network is trustworthy,
Top 12 Best Zero Trust Security Solution Providers
HASHICORP
HashiCorp delivers consistent workflows to provision, secure, connect, and run any infrastructure for any application.
Enable scalable, dynamic security across clouds
- Improve enterprise security posture
- Reduce the likelihood of a breach
- Accelerate secure multi-cloud adoption
Adopt Zero Trust Security across clouds with these four pillars
- Machine authentication & authorization
- Machine-to-machine access
- Human access and authorization
- Human-to-machine access
AKAMAI
Akamai Connected Cloud keeps applications and experiences closer to users and threats farther away.
- Strengthen your security posture
- Free up your security team to focus on business
- Gain insight on emerging threats
ZSCALER
The Zscaler Zero Trust Exchange, the true zero trust platform securely connects users, workloads and devices against exposure to corporate networks.
- Protect against cyberthreats and data loss
- Provide fast, direct, and secure app access and digital experience monitoring
- Eliminate management overhead and the cost of point products and appliances
NETSKOPE
Netskope empowers the largest organizations in the world with the right balance of protection and speed they need to enable business velocity and secure their digital transformation journey.
- Accelerated business agility
- Security without performance trade-offs
- Reduced security risk
- Improved security posture
- Reduce total cost of operations
F5
F5 Distributed Cloud platform delivers improved functionality, advanced security, and more simplified operations than native services from cloud providers.
- Continuously review and assess access, threats, and trust
- Provide visibility into application access and traffic trends, aggregate data for long-term forensics, accelerate incident responses, and identify issues and unanticipated problems before they can occur
- Initiate quick action, if required, including the termination of specific access sessions
- Deliver a fast overview of access health
DUO
Duo protect your workforce and user data from cybersecurity risks with Multifactor Authentication (MFA), Two-Factor Authentication (2FA) and a Single Sign-On solution.
- Security Overload for End-Users
- Workforce Decentralization
- Environmental Complexity
- Streamline User Experiences
- Protect a Diverse Workforce
- Secure Remote Work
SOLO.IO
Solo.io Industry’s Leading Cloud-native Networking Platform for APIs, Containers and Cloud Built on Kubernetes, Istio, Envoy, GraphQL and Cilium
- Zero trust security for APIs and application ingress with an API Gateway
- Zero trust security for distributed applications with a service mesh
Citrix DaaS, Citrix Secure Private Access, Citrix Analytics for Security
Citrix workspace software delivers the business technology that creates a simple, secure and better way to work from anywhere and on any device.
- Assessing existing cybersecurity controls and determining the key network flows and vulnerabilities
- Determining a protected surface that will be shielded from harm through zero trust measures
- Implementing specific technologies such as adaptive and multifactor authentication, VPN-less proxies, and secure embedded browsers
- Continuously monitoring the network to keep tabs on suspicious activity and fine-tune the solution mix and overall cybersecurity approach as needed
FORTINET
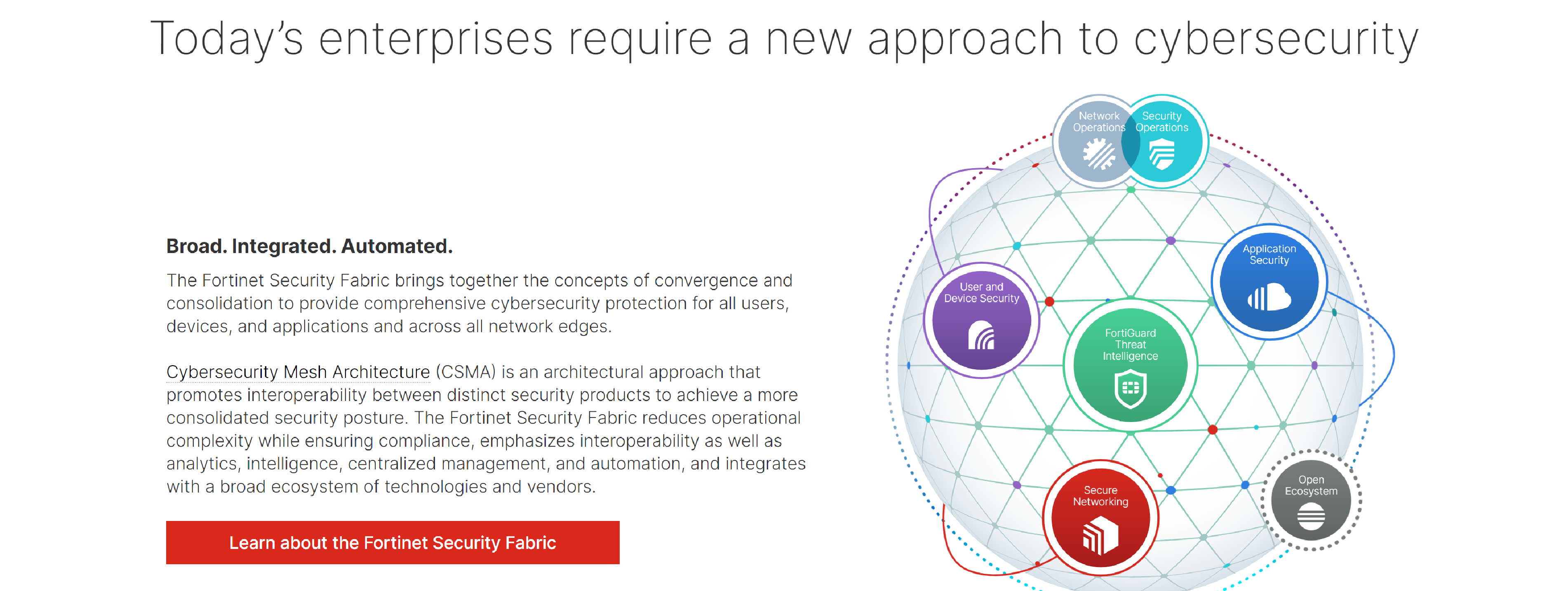
Fortinet Universal ZTNA provides secure and simple access to applications, regardless where they are located, for users working from anywhere.
- Enables ZTNA policies to be enforced for both remote workers and on-site workers
- Grants access to a specific application only for that session
- Verifies the user identity, the device identity and posture, before granting access to an application
- Provides both secure access and endpoint protection with a single, unified agent
- Allows moving from VPN to ZTNA over time, as a free feature of FortiOS 7.0 and above
- Establishes TLS encryption automatically between endpoint and access proxy, hiding traffic
LOGRHYTHM
LogRhythm SIEM platform effectively unifies log management, security analytics, case management, and incident response.
- Detect Threats Earlier and Faster
- Gain Visibility Across Your Environment
- Easy to Use
- Build for Today, Scale for Tomorrow
YUBICO

Yubikeys enable phishing-resistant user identity verification before providing access.
- Accelerate Zero Trust with strong authentication
- Trusted user identity using phishing-resistant modern MFA
- Build a great user experience with passwordless that drives productivity
OKTA
Okta’s identity platform is easy-to-use, neutral, and works with your existing solutions, so you’re free to choose the best technology for now and the future.