Access governance software is a system used by organizations to manage user access to information technology (IT) assets, such as applications, databases, and network resources.
Discover the top 12 best Access Governance Software Tools
NETWRIX
Reduce the chance of data breaches by making access to sensitive data exclusive with data access governance software from Netwrix.
- Focus your data security efforts on the most critical data
- Monitor security risks and report your progress
- Identify the most significant risks around your data and close those gaps first
- Prove the security of personal information and respond promptly to DSARs
AVATIER
Avatier access governance software compliance auditor features access certification and group enforcer automates group management software for governance risk and compliance management.
- Reduce Costs
- Increase Productivity
- Achieve Compliance
- Increase Security
- Wizard-Enabled
- Prevent Mistakes
ONEIDENTITY
One Identity provides data access governance tools to help control access and govern data through automated requests.
- Protect and identify high-risk areas
- Empower data owners to control access
- Power to approve unstructured data-access requests
- Detect and remediate policy violations
- Automate request-and-approval workflow
- Analyze unstructured data access requests to files, folders, NAS and SharePoint
SAP
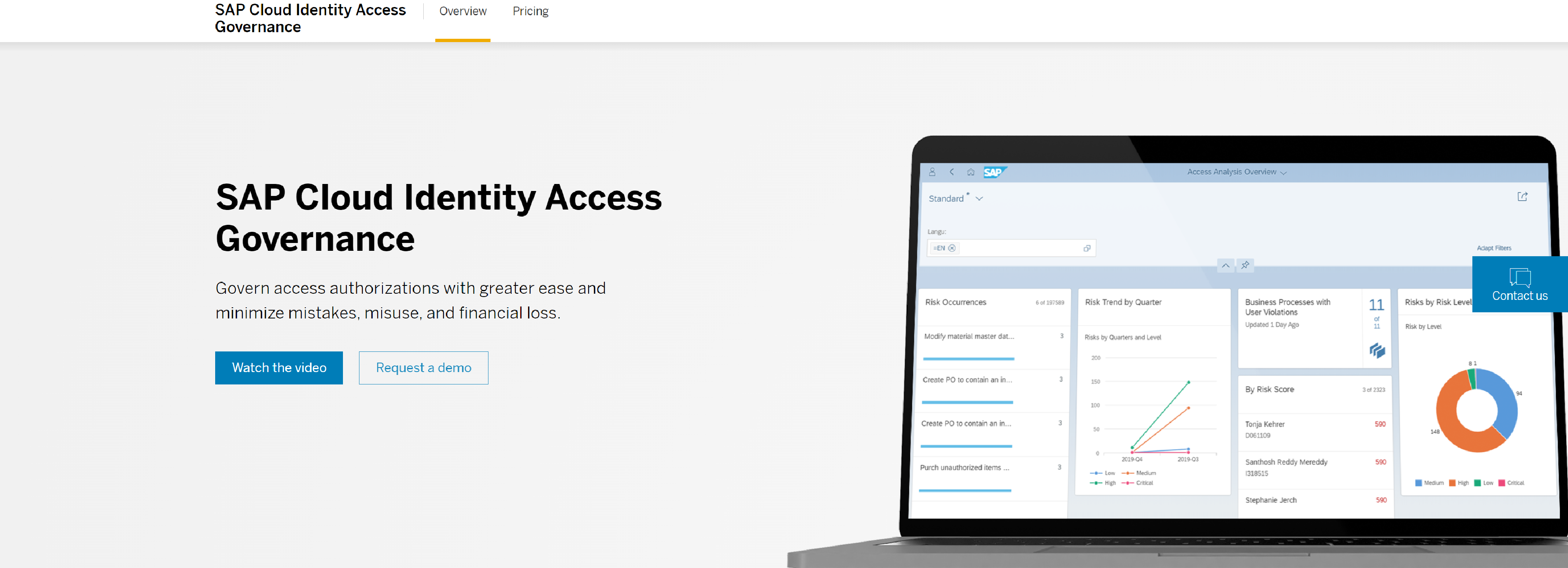
Streamline identity and access management (IAM) in complex on-premise and cloud environments with SAP Cloud Identity Access Governance software.
Features:
- Access compliance management
- Intelligent optimization of assignments
- Extended control and risk management
Benefits:
- Simplify the governance of data access
- Deliver a seamless user experience
- Adapt identity and access governance
LEPIDE
Lepide’s Data Access Governance Solution enables you to know where your sensitive data is, who and how users are accessing it.
- Classify Sensitive Data
- Stop Unauthorized Access
- Monitor User Behavior
- Detect Anomalies
- Detailed Pre-Set Reports
- Real Time Alerting
ITCONCEPTS

ITConcepts is one of the leading IT service providers for the efficient automation of IT business processes. ITSM, ITOps, IAM & Big Data.
- Reduced risk of unauthorised access to sensitive data
- Improved audit performance
- Lower operating costs
- Increased productivity for IT staff
LUMOS
Govern your apps with one platform with Lumos SaaS management and identity governance software.
- Automate Your Helpdesk
- Increase Your Security Posture
- Simplify Compliance
- Spend Less On SaaS
STEALTHBITS
Stealthbits protects unstructured data & sensitive information with data governance tools and data access governance software.
- Unstructured & Structured Data Support
- Active Directory Management & Security
- Desktop & Server Security
SAVIYNT

Embrace Zero Trust, secure sensitive & privileged access, and stay in continuous compliance with the world’s #1 cloud identity governance platform.
- Protect Critical Assets
- The Right Access, at the Right Time
- Make Smarter Security Decisions
- Solve Big Identity Challenges
- Reduce Risk & Compliance Costs
OVALEDGE
OvalEdge enables its customers to take a full-circle approach to overcome common data access roadblocks.
- Enforcement of data access policies just got easier
- The only integrated & non-intrusive data access platform
- Enforce your data access policies with a few simple steps
- OvalEdge Recognized by Industry’s Top Analysts & Thought Leaders
TORSIONIS

Simple, intelligent and effortless Data Access Governance for Microsoft 365. As users constantly share data, Torsion delivers powerfully.
- The Automated Solution
- Simple, intelligent and effortless Data Access Governance for Microsoft 365
- As users constantly share access, ‘who has access to what’ quickly gets out of control
SECURENDS
SecurEnds cloud software enables the world’s most forward-thinking companies to automate user access reviews, access certification and recertification, and entitlement audits.
- Establish a clean set of user entitlement data to support risk and compliance efforts
- Increase compliance efficiency by streamlining certification
- Automate data and controls ingestion and approval workflows
- Interactive, identity-centric view across IT risks, applications, and entitlements
- Out-of-the-box application support and IT controls
- SaaS-based platform for rapid delivery for quick time-to-value